IDSync
Microsoft Tightens Azure AD’s Access Controls for SaaS Apps
eWEEK content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More. The Tenant Restrictions feature in Azure Active Directory ...

Control access with the perimeter security layer
Welcome to part two of our seven layers of security miniseries. In this episode, our Cyber Security Specialist Scott Harrison shares tips and insights on how to make your organisation's digital perimeter safe from threats. Ensure only the right people get access to your data and systems. It's all about identity management.

Ensurity Identity & Authentication Solutions
Ensurity Identity & Authentication Solutions help you protect users, apps, and data with strong, easy-to-use security. From MFA to passwordless login, Ensurity makes access safe and smooth for every business. Build trust, stop threats, and simplify identity management with a smarter security approach. Start securing your digital world today.

Show HN: StegCore – a decision boundary for AI systems (truth ≠ permission)
TL;DR
Most systems treat “verified” as “allowed.”
StegCore separates those concepts.StegCore is a small, docs-first project that defines a decision boundary:
given verified continuity (from an external system), it answers allow / deny / defer, with explicit constraints like quorum, guardian review, veto windows, or time-locks.No policy engine yet. No AGI claims. Just the missing layer.⸻The problemModern automation — especially AI-driven automation — usually collapses three things into

The ins and outs of Apple identity management in the enterprise
In today’s cloud-enabled world, enterprise identity management is a fact of life — and in the Apple ecosystem, particularly for macOS, it can get confusing. Here’s what to know. It used to be simple: ...
Access Control Gap in Microsoft Active Directory Widens Enterprise Attack Surface
An access control gap in Microsoft's Active Directory (AD) service may allow users within Windows environments to access domains beyond those for which they are authenticated, all while IT admins are ...

Identity-based attacks need more attention in cloud security strategies
As businesses migrate more of their assets to cloud platforms, identity management has risen to the top of the list of important security practices. Many sophisticated hackers use stolen credentials ...

Automatic Identity Management for Entra ID on Azure Databricks
Automatic identity management enables you to seamlessly add users, service principals, and groups from Microsoft Entra ID into Azure…

Self-Hosting a Password Manager on a Raspberry Pi
In this instructional I’m going to show you how to host your own password manager within a Docker container on a Raspberry Pi.
When ransomware hijacks your active directory: an executive playbook
Active Directory compromise can devastate operations. This playbook outlines how to contain, investigate, and recover.
When ransomware hijacks your active directory: an executive playbook
When ransomware hits, the instinct is to get systems back online as quickly as possible. But if the attack is on your Active ...

The AI Agent Identity Crisis: Why Your IAM Strategy Needs a Machine-First Redesign
While you perfected human identity management, machines quietly took over your infrastructure. AI agents now handle 70% of identity transactions, but most IAM strategies still treat them as afterthoughts. This creates dangerous security gaps that attackers actively exploit. Time to redesign.

How Event-Based Identity Management Can Enable Dynamic Security
Explores how event-based identity management enables real-time access control, continuous assessment, and Zero Trust in IAM.
Azure Active Directory Access Control Features Previews Released
Privileged Identity Management for Azure AD roles-based access control (requires Premium 2 subscription) An access reviews process to affirm user needs for accessing applications and groups (requires ...

Digital Identity Management
Mastering robust digital identity management is crucial for cybersecurity and secure system access. This expert guide delves into core…

10 Best Frontegg Alternatives for Seamless Identity Management
In today’s digital landscape, businesses require reliable and secure customer identity management platforms that ensure smooth user…
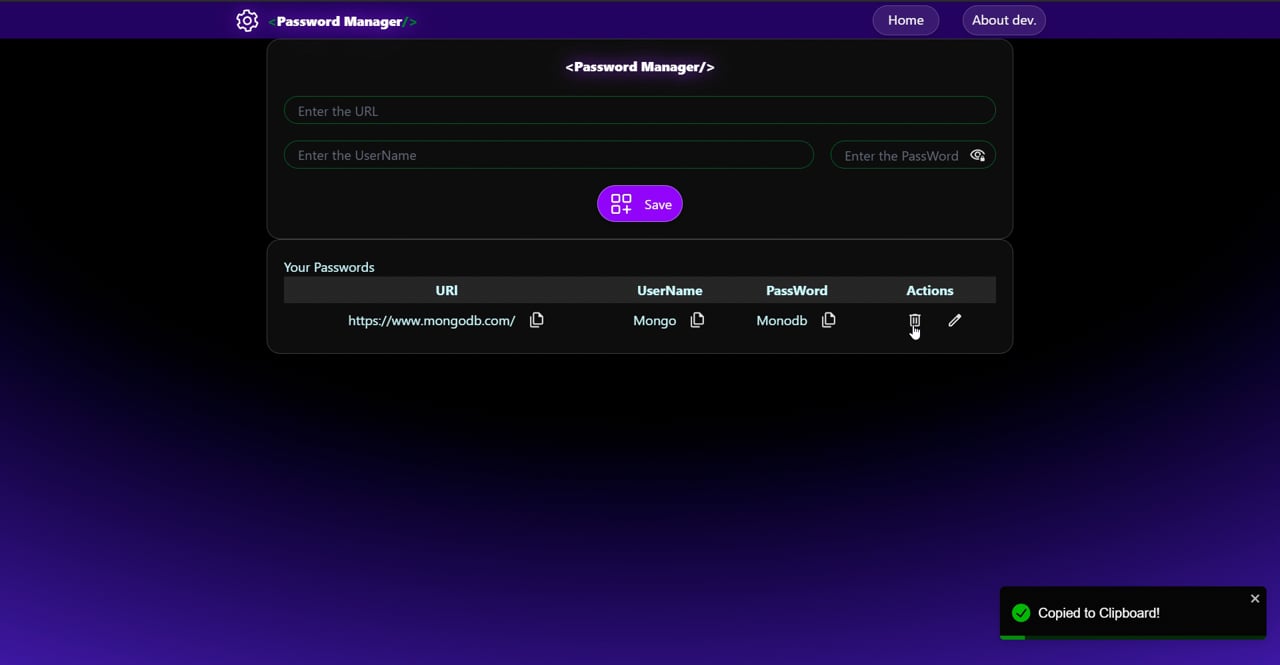
Password manager
This password manager is secure use local storage , easy to use

Why Identity Management is Key in a Cyber Resilience Strategy
Identity compromise is one of the top cyber threats to organizations, prompting cybersecurity professionals to encourage better identity management hygiene across industries. According to the Identity ...

Microsoft Launches Azure Active Directory-Based Access Control for Service Bus
In a recent statement, Microsoft has announced the general availability of Azure Active Directory (AD) based access control for Service Bus, enabling the option to use identities in combination with R

Building Identity Management That Drive Innovation
Building Identity Management That Drives Innovation
In today's fast-evolving digital landscape, identity management (IdM) is often…









